Cyberattack hits nearly 100 countries
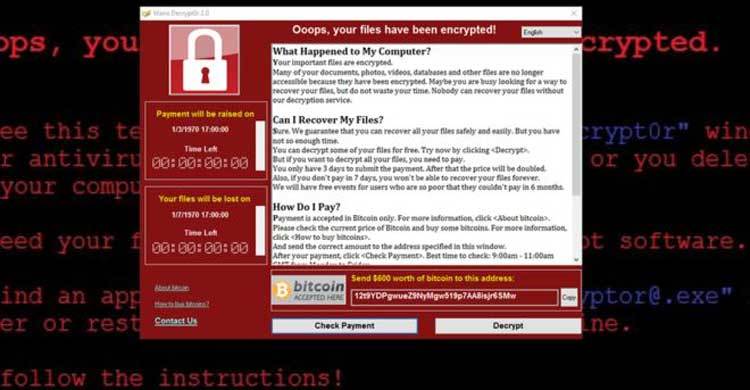
A large-scale cyberattack affected nearly one hundred countries and held tens of thousands of computers ransom throughout the day on Friday.
Antivirus provider Avast reported that at least 75,000 computers had been infected by the crippling malware and that the "WanaCrypt0r 2.0," as it is called, ransomware had been detected in 99 countries.
More than a dozen hospitals in England and major companies, including FedEx and Spain`s largest telecom, were targeted Friday.
U.S. companies were being warned to gird against the threat, which reportedly blocked access to computers in exchange for a ransom.
At least 16 National Health Service hospitals and related organizations were affected in England and another five in Scotland, officials said in a statement.
British Prime Minister Theresa May said the government`s cyber security arm was working with the NHS, and confirmed that "no patient data has been compromised."
The extent of the attack globally and the author of the malicious software — known as the Wanna Decryptor, or WannaCry — were unclear, but cyber security experts said they were surprised at its apparent reach.
"The scale of it — that`s pretty unprecedented," Ben Rapp, the CEO of IT support company Managed Networks, told NBC News` British partner ITV News. "There`s been a lot of ransomware in hospitals, but to see 16 hospitals, last time I looked, and reports of other people — this is probably the biggest ransomware attack we`ve seen."
In a statement to NBC News, FedEx said that "like many other companies, FedEx is experiencing interference with some of our Windows-based systems caused by malware. We are implementing remediation steps as quickly as possible."
The Memphis, Tennessee-based global delivery company did not immediately say whether a ransom was demanded for return of their computers` functions.
The U.S. Department of Homeland Security said Microsoft released a patch to address the vulnerability in March and urged users to install it.
Some English hospitals tweeted that they were taking precautionary measures to protect patients, while doctors` offices tweeted problems obtaining patients` files because of the attack.
The NHS blamed the Wanna Decryptor for infecting computers — an encryption-based ransomware that locks a system and its files from use unless money is paid to hackers for access. It`s typically spread through email phishing programs and affects computers using Windows operating systems.
The program is especially nasty because it acts like a worm — finding security holes in a computer to spread throughout a network.
It could take days before a company cleans up its system and is fully functioning again, security experts say.
But sometimes, hackers hit the jackpot: Last year, Hollywood Presbyterian Medical Center forked over $17,000 after suffering a ransomware attack.
The IT systems of NHS sites were reportedly bombarded by pop-up messages Friday demanding such a ransom, and purported screenshots showed the cyber attacker asking for "$300 worth of bitcoin" — a form of digital currency — to be sent to a certain online address.
"It`s a small ransom," said Gene Spafford, founder and executive director emeritus of Purdue University`s Center for Education and Research in Information Assurance and Security. "But if you set the price too high then many of their victims won`t pay."
Spafford said ransomware typically targets those without strong security in place, such as home users and small companies.
Hospitals and larger companies might be susceptible, he added, if they`re slow to fully upgrade their networks or use pirated programs.
This particular ransomware is "using this flaw in the file-sharing that is giving it apparently a real boost," Spafford said.
He added that companies are at the mercy of the hackers, who could decide if their ransomware becomes too big they might decide "not to cash out because they`re worried about being traced" and tipping off authorities about their whereabouts.
Spanish telecom giant Telefonica confirmed in a statement that a "cybersecurity incident" occurred Friday that affected the computers at its Madrid headquarters.
A Telefonica spokesman told Reuters that a window appeared on its computers also demanding a bitcoin payment in order to regain control.
Spain`s National Cryptology Center said that an attack had been launched "against various organizations" in the country through their Windows systems, and other companies were taking preventative measures.
It wasn`t just companies affected by this particular ransomware.
The mayor of the small community of Timra, Sweden — population 10,000 — told Reuters it has "around 70 computers that have had a dangerous code installed."
Josh Feinblum, vice president of information security at the cybersecurity company Rapid7, said companies should back up data and ensure their systems are as up to date as possible. He said the speed at which the ransomware spread is unusual.
"I think what was unique about this ransomware is that it essentially used a security flaw in a very common set of software that allowed it to self-replicate across the facilities and environments that it was in," Feinblum said.
"And that`s not very typical in the ransomware world and that`s something that we haven`t really seen at scale in a long time," he said.
Source: Agencies


